Mac Address Spoof Hacking
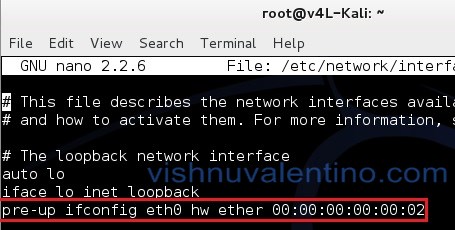
How to avoid being hacked and how can I figure out that somebody hacked into my tablet or into my network.. That’s because your ISP could easy trace you by two simple information which is the time and IP Address.. x x x and y y y y Lets say you are using the device with mac address yy:yy:yy:yy:yy:yy to spoof xx:xx:xx:x.. If you think you’re safe hiding behind a proxy server, bad news is most proxy server has logging enabled and your IP address is definitely listed in the log file when you’re connected to it. Hanson Electronic Scales Manual
is mac address spoofing illegal
How to avoid being hacked and how can I figure out that somebody hacked into my tablet or into my network.. That’s because your ISP could easy trace you by two simple information which is the time and IP Address.. x x x and y y y y Lets say you are using the device with mac address yy:yy:yy:yy:yy:yy to spoof xx:xx:xx:x.. If you think you’re safe hiding behind a proxy server, bad news is most proxy server has logging enabled and your IP address is definitely listed in the log file when you’re connected to it. e10c415e6f Hanson Electronic Scales Manual
is mac address spoofing illegal Crack Photoshop Cs6 For Mac Os
One of it is your network adapter’s MAC address Every network card contains a unique code called MAC address that is permanently assigned to it, similarly like every computer requires a unique IP address to be connected to a network.. So you’ll need to use proxy or even chains of proxies to avoid being directly traced by the victim’s firewall.. Don’t forget, there are still some other important information that can be obtained from an IP Address if a person knows what tools to use.. When you’re going to hack a computer or server on the Internet, you won’t want your IP address to spill out.. In simple words, a MAC address can be used to uniquely identify your Android phone on the Internet or the local network. Brother Dcp-130c Driver Download Win7